The Four Stages of Key Management Maturity: How Do You Rank?

“You need a key management strategy that secures your data and streamlines IT management.”
When your organization relies on encryption, you know first-hand that an effective key management solution can be the difference between tragedy and triumph. Each of your business applications uses dozens to hundreds of cryptographic keys for encryption. The right key management solution provides essential security for your applications.
A “mature” key management solution can extend your horizon of cryptographic possibilities further, helping you secure data, streamline IT management, and rapidly scale operations. Though all organizations recognize the importance of protecting their infrastructure with key management, gaps exist in many security postures.
In the 2023 Data Breach Investigations Report, 26% of data breaches involved web applications, with ¾ of organizations reporting app security was a concern. So, what steps can you take to improve your organization’s key management, and why is that so important?
In this article, we:
- Spotlight security assumptions that can put you at risk,
- Help you identify your organization’s current level of key management maturity,
- Outline the structured approach necessary to maturing your key management.
Encryption Key Management Maturity Stages:
Common misconceptions that put you at risk
- “Cloud services are automatically secured”: to safeguard your information from potential threats, it’s essential to enable encryption features.
- “Compliance equals total security”: while compliance is important, it alone does not guarantee the security of your data. Protecting yourself against the wide range of cyberattack vectors requires you to implement effective key management.
- “Key management is optional”: in reality, any organization with applications that use encryption needs to manage them, and spreadsheets are not the answer. Underestimating key management complexity and scale opens new avenues for potential cyberattacks.
What is key management?
Whether data encryption is encoded on storage media at rest or encrypted data is protected during transmission, encryption keys are the only way to unlock that data. Organizations with multiple applications and cryptographic solutions generate tons of encryption keys over time.
So, what do you do with all those keys? One thing is certain: you need to implement a key management strategy that protects your cryptographic keys and reduces management overhead.
Common Key Management Challenges
- Cryptographic Sprawl, aka “too many keys to manage”: organizations with multiple applications running encryption will generate keys faster than they can manage. Spreadsheets are not the answer; from a scalability and security standpoint.
- Secure key sharing: when two entities need access to the same key, secure key sharing becomes critical to maintaining security. From a logistics perspective, sharing a key without proper safeguards creates vulnerabilities.
- Lack of key management expertise or proper tools: the best intentions to secure your keys can be compromised with substandard tools and methodologies.
A robust key management solution allows you to define how keys are created, distributed, rotated, stored, and destroyed. It gives you visibility and control over your encryption keys, safeguarding your data from unauthorized access. Good key management enables you to streamline business applications, secure secrets, and keep sensitive data safe.
What makes key management mature?
Mature key management is centralized, automated, well-integrated, and hardware-backed.
Centralization
Centralized key management offers a secure foundation by consolidating key storage and access control, reducing the risk of unauthorized access or key loss.
Automation
Automating the key lifecycle, including generation, distribution, rotation, and retirement, ensures consistent and error-free management, minimizing human error vulnerabilities.
Integration
Application integration streamlines your cryptographic operations, seamlessly embedding encryption functions into your business applications while maintaining encryption key security.
Hardware-backed
Hardware-backed key management solutions enable organizations to store keys in secure cryptographic devices, such as hardware security modules (HSMs). Hardware-backed solutions provide safe environments to store keys separately from other data, shielding them from possible threats.
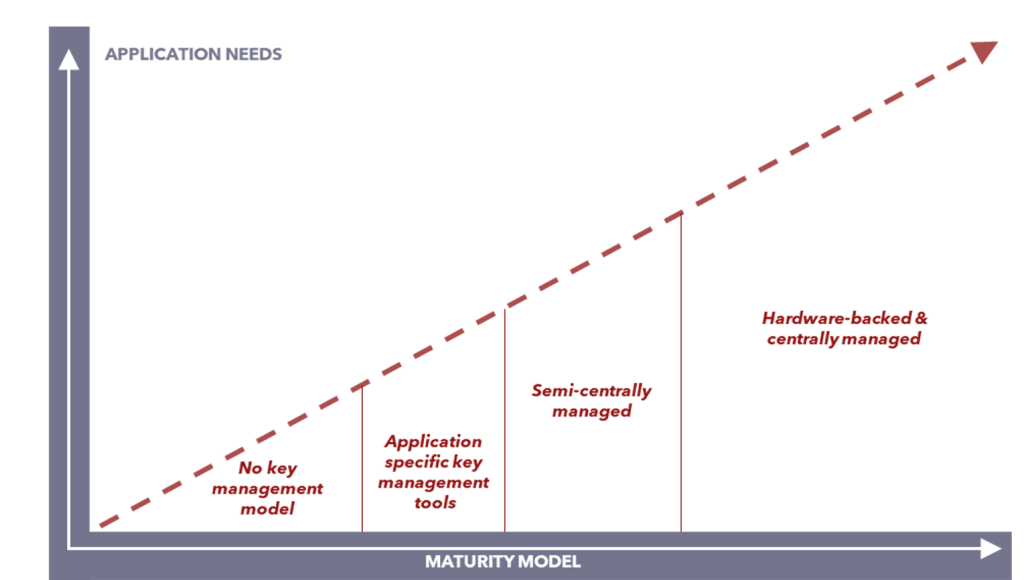
The journey to the top
It is essential to evaluate all the aspects of key management to know where your organization stands and plan your data security roadmap.
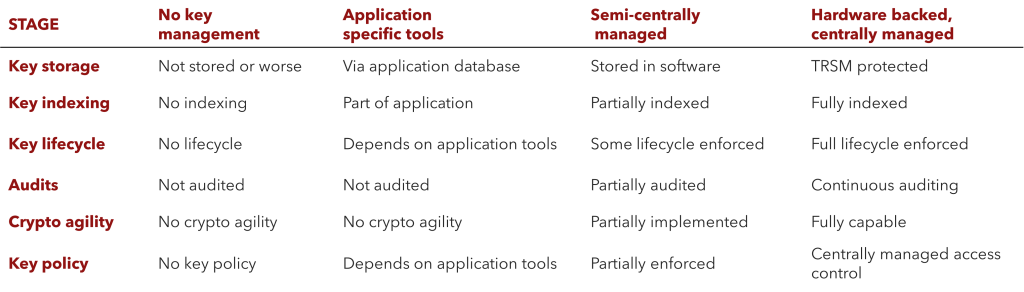
Stage 1: No key management
Initially, organizations with encryption tools may still need to integrate a key management solution. In this early phase, keys are neither stored nor audited, with no key policies set to manage their use. Some organizations will rely on software encryption programs that run from a kernel on their hard drive, exposing them to a wider range of cyber threats.
While any encryption is better than none, if you think your organization is in this first phase, it is imperative to talk with a cryptography provider.
Stage 2: Application-specific tools
Some business applications include their own key management tools. While this is certainly better than not using key management, it’s not ideal because the application stores keys in a database. Application-specific key management tools tend to partially index keys and rarely, if ever, perform audits. The user often lacks control over these features, nor can they determine key lifecycles and policies.
This stage provides a bare minimum of security at an application level. However, it leaves you without the ability to control key creation, distribution, rotation, storage, and destruction.
Stage 3: Semi-centrally managed
This stage is characterized by partiality: keys are partially indexed, their lifecycles are partially managed and partially audited, and key policies are only partially enforced. Organizations in this stage commonly store their keys in software. Doing so is better than nothing, but software-based cryptography is not ideal, as cryptographic keys have no physical protection or separation.
Overall, organizations in this stage enjoy increased agility. However, when it comes time to scale operations, that agility reaches its limit sooner rather than later.
Stage 4: Hardware-backed, centrally managed
Organizations that have reached the highest level of key management maturity have implemented hardware-backed solutions managed through a centralized platform. Keys are fully indexed, their lifecycles are managed, policies are defined and enforced, and keys are stored in dedicated, physically secure hardware components such as an HSM or Cloud HSM.
Organizations in this stage benefit from total control and full cryptographic capability and agility.
FAQ
What are the misconceptions about key management are and how do they pose security risks?
Three key misconceptions about managing encryption keys are: the assumption that cloud services inherently secure data, the belief that compliance ensures complete security, and the idea that key management is optional. These misconceptions can leave organizations vulnerable to cyber threats.
How does key management maturity affect data security and operational effectiveness?
Key management maturity significantly influences an organization’s data security and operational efficiency. Advancing maturity levels enable better control over encryption keys, reducing unauthorized access and data breaches. Mature key management involves centralized, automated processes integrated into business operations, enhancing overall security and effectiveness.
Can you summarize the stages of key management maturity and their associated characteristics and challenges?
The stages of key management maturity are:
- Stage 1: No key management, lacking policies and control over key usage.
- Stage 2: Application-specific tools, providing limited control over key lifecycles.
- Stage 3: Semi-centrally managed, with partial key management and enforcement.
- Stage 4: Hardware-backed, centrally managed, offering full control and security over encryption keys.
Each stage presents its own challenges and benefits, with higher stages providing greater security and control.