What are digital signatures?

When it comes to sharing data, few things are as important as trust. Without trust, real data security just doesn’t exist.
Digital signatures are one of the most reliable ways to create trust between senders and receivers of data. They authenticate data and anyone who needs to access it. If a handwritten signature proves the authenticity of physical objects, like contracts or works of art, then a digital signature proves the authenticity of digital objects like messages, files, applications, and code.
Simple enough—but like many concepts in cryptography, we don’t always have to understand the nuts and bolts so long as the process works. In this article, we’ll explain digital signatures and the digital signing process so that you can be a subject matter expert too.
The digital signing process
Digital signatures are created by a process that involves hash functions, private encryption keys, and algorithms. The National Institute of Standards and Technology (NIST) specifies a set of algorithms that can be used to create digital signatures. In addition to creating signatures, a digital signing algorithm typically includes algorithmic processes to verify signatures and create asymmetric key pairs.
Here’s how it works
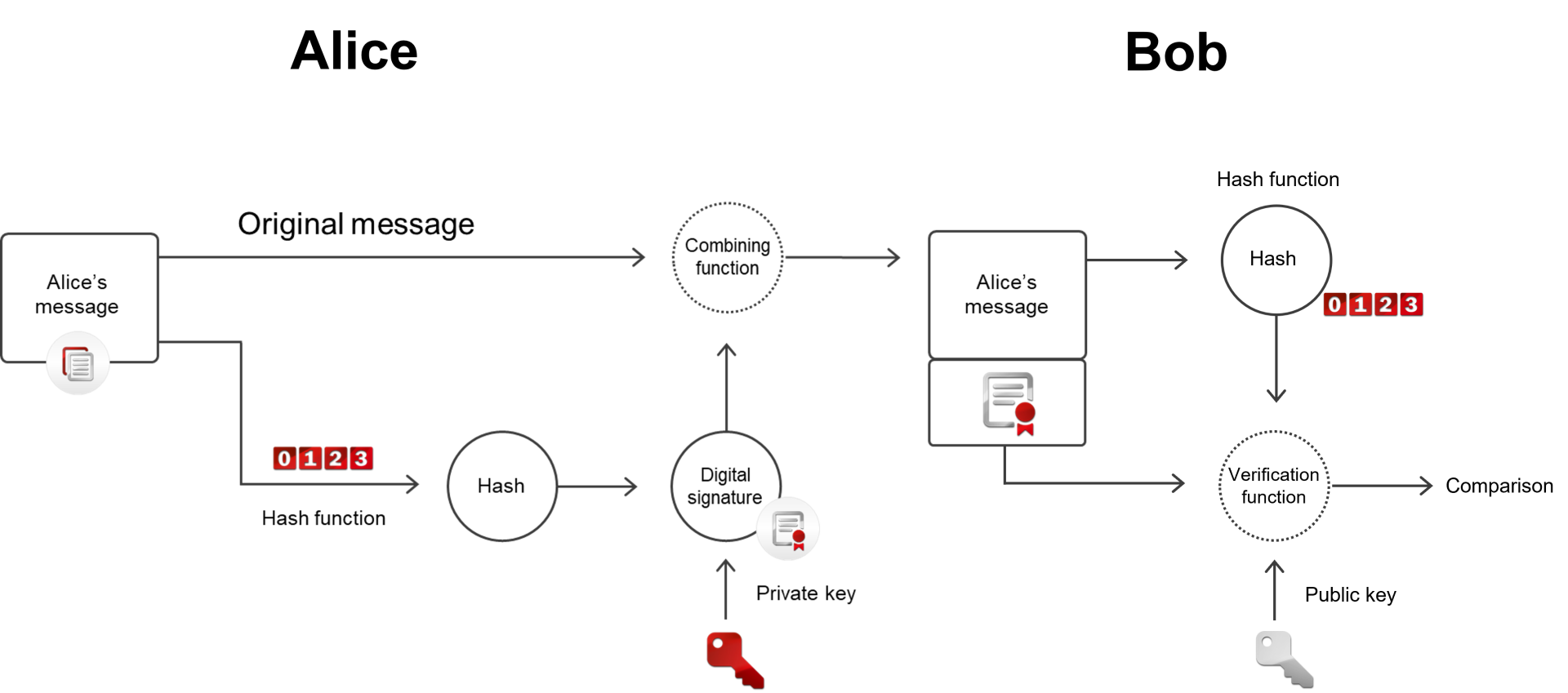
Let’s say Alice sends a message with a digital signature to Bob. Because there is already trust between Alice and Bob, Alice has a private key to encrypt the message, while Bob possesses Alice’s public key to decrypt it. First, the plain text data of Alice’s message is processed by a hash function to convert it to a hash code. A signing algorithm then combines the hash code with Alice’s private key to generate a digital signature. This digital signature is combined with Alice’s original message and then sent to Bob.
When Bob’s computer receives Alice’s digitally signed message, it processes Alice’s original message with an identical hash function and compares it with the hash that Alice’s computer produced. Then it determines whether the two hash values are equal. It also applies the public key Bob has with the private key in Alice’s message. If the public and private keys are compatible, and if the two hash codes match, then the signature is valid and Alice’s message is verified. As a final result, trust is established between Alice, her message, and Bob.
In short, the digital signing process uses plaintext data, hash code, and asymmetric encryption keys to generate a digital signature that proves the validity of data. Digital signatures can contain other pieces of data, too. For example, a signature can include a timestamp to show when it was sent. That way, if the sender’s private key is ever compromised, previously signed materials can still be authenticated in retrospect.
Private and public encryption keys
A key (no pun intended) aspect of the digital signing process is asymmetric encryption. Asymmetric encryption involves pairs of encryption keys that work together to securely share data. Evert asymmetric key pair consists of a private key and a public key.
The private key encrypts data on the sender’s side while the public key decrypts that data on the receiving end. As the name suggests, the private key must be kept absolutely secret to ensure that only the sender can digitally sign the data they send. The public key can be used by any authorized recipient to decrypt and validate the data.
Asymmetric encryption is typically handled by a hardware security module (HSM) in enterprise setups. These cryptographic devices provide physically and logically secure environments in which to perform cryptographic operations, such as key generation and encryption. Devices like these do the cryptographic heavy lifting in the digital signing process.
Code signing
Digital signatures are often used to distribute files, transact payments, and to secure communication across organizations. However, a major use case for digital signatures is code signing.
Deploying a code signing solution allows organizations to cryptographically sign firmware and software on-demand. Whether this is for software products or software used to interact with IoT devices, the process is the same. Digitally signing code helps developers distribute software that can be authenticated by the user, maintaining both security and trust.
Deployment
While the signing process may seem complex, it is fairly simple to deploy. HSMs and key management solutions can generate asymmetric keys, encrypt/decrypt data, manage and store certificates, and define security policies for the process. These solutions can be deployed as on-premises appliances or through an HSM-as-a-Service model (cloud HSM). Deploying them on-premises provides more hands-on control, while cloud solutions tend to offer faster deployment and reduced capital expenditures (CapEx).
Conclusion
We hope this article has clarified a few things about digital signatures and how they work. Feel free to contact our subject matter experts if you have any further questions about this topic, or if you’d like to discuss anything related to data security and cryptography.
Secure digital signing solutions use HSMs to create asymmetric key pairs, perform encryption functions, and physically protect private keys. Digital signing algorithms produce digital signatures, and can include logic to verify signatures and create keys. All of these components work together in the digital signing process. Go through a trusted cryptography provider to deploy a digital signing solution.
In most countries, digital signatures carry the same legal weight as handwritten signatures. In the United States, the legal status of digital signatures was established by the Electronic Signatures in Global and National Commerce Act (E-Sign Act). This 2000 federal law provides a framework to determine the validity of electronic signatures.
A digital certificate is an electronic file. It normally includes an encrypted hash code of the signer’s message. The signer’s private key is affixed to the signature, so that the receiver can use a public key to decrypt the information.
Digital signatures are necessary to prove the validity of digital objects, as well as authenticate their creators. Digital signatures create trust between users and machines on a network, strengthening security and reducing cyber risks.