Hashed or Unhashed Token Generation
The KMES Series 3 enables customizable token generation profiles, offering diverse options and parameters for seamless integration.
Streamline data handling for effortless data protection

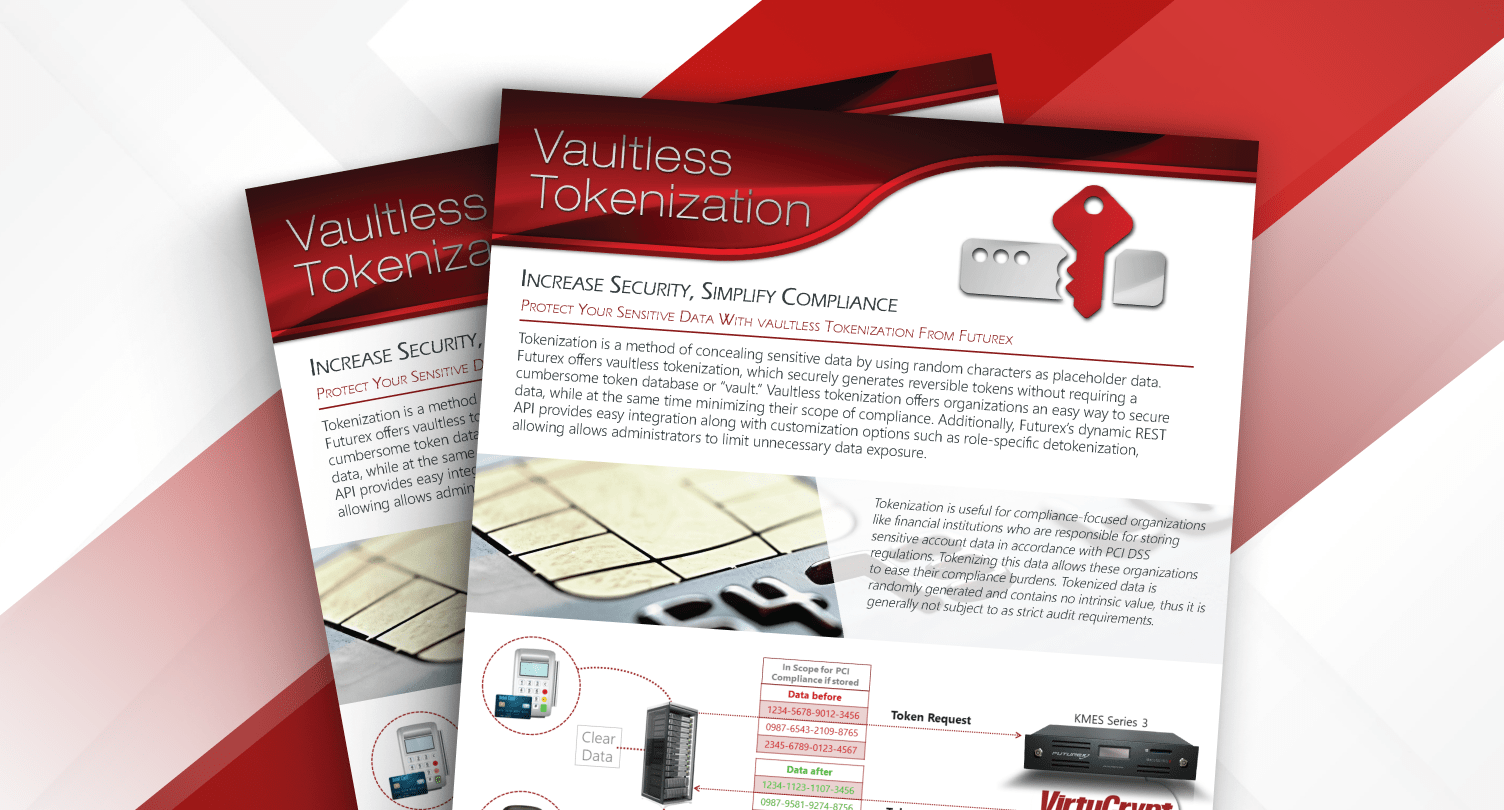
Tokenization secures sensitive data by replacing it with randomized tokens, reducing security risks. However, storing tokens with data exposes vulnerabilities. Futurex's vaultless tokenization enhances security and eliminates complexities and risks associated with token vaults. Ideal for merchants and organizations seeking to streamline compliance, cut costs, and fortify security.
Reduce breach risks and maximize encryption security for all transactions from point of entry to decryption
Simplify security architecture and reduce the attack surface by removing centralized token storage
Reduce compliance costs and efforts by limiting sensitive data exposure, reducing PCI DSS audit scope
Ensure smooth integrations that enhance security and boosts operational efficiency
The KMES Series 3 enables customizable token generation profiles, offering diverse options and parameters for seamless integration.
Futurex tokenization utilizes format-preserving encryption algorithms for effortless integration into existing environments without database modifications.
Tokenization replaces sensitive data with surrogate values, rendering them meaningless to fraudsters. Tokens serve as references linked to sensitive data, enhancing security.
Tokenization is a great way to protect sensitive data like credit card details by using randomly generated substitute characters as placeholder data.
Vaultless tokenization offers organizations an easy way to secure data, while at the same time minimizing their scope of compliance.
Tokenization streamlines audits for organizations complying with PCI DSS and other mandated standards.
Vault tokenization is the older method of tokenization. In the vault tokenization model, detokenization requires a database that is queried with a token to retrieve the original data stored within. This requires large databases mapping tokens to their corresponding clear data. These databases are known as token vaults. Retrieving and detokenizing vaulted data takes extra time because of the need to query vault database for the corresponding token. Predictably, this creates latency issues for large databases supporting frequent queries. There are implementation, security, and compliance drawbacks to the vault tokenization model as well. Token vaults represent a single point of failure in tokenization infrastructures. They are a high-risk target for theft since they contain highly sensitive data in the clear. Possessing clear data brings you within the scope of PCI DSS compliance, which could be avoided otherwise. Furthermore, large token vaults often present complex implementation problems, particularly in distributed, worldwide deployments.
Vaultless tokenization allows organizations to easily meet international regulatory compliance obligations. How? By reducing or even eliminating the presence of clear-text cardholder data from their processing infrastructure and storage environments.
Vaultless tokenization eliminates the need for a token vault or vault database. The vaultless tokenization process involves secure cryptographic devices (such as Futurex’s Key Management Enterprise Server (KMES) Series 3) to generate tokens using standards-based algorithms and encryption keys.
In this model, sensitive data remains encrypted throughout the payment process, which potentially eliminates cleartext cardholder data from the merchant network entirely. The process of creating tokens can be fully automated.
For example, with vaultless tokenization, when a card is presented at a Point-of-Sale terminal, the primary account number (PAN) is immediately encrypted using Point-to-Point Encryption (P2PE). When the encrypted PAN is sent from the POS terminal to the secure cryptographic devices on the back-end, it is decrypted within the devices’ secure boundary, tokenized, and then processed through the card issuer using the tokenized data.
Under this model, the combination of P2PE encryption and vaultless tokenization allows for secure transaction processes and storage of credit card details for future use, without ever placing cardholder data in the clear. Sensitive data stored via vaultless tokenization also does not have to be replicated between data centers, resulting in reduced latency.
The proven success of tokenization has applications across multiple industries and sectors. It can be expected that a wide range of organizations, from healthcare providers to government agencies, will take advantage of the myriad of benefits of using the versatile and powerful vaultless tokenization technology.
There are still some financial corporations that rely on vault tokenization to secure their customers’ sensitive payment information, despite the drawbacks to the method. This is typically due to outdated regional legislation or issues in the wording of encryption laws. For example, local legislation may specify that all financial corporations must use “tokenization done in a vault database” without realizing that they are eliminating those corporations’ ability to use a more secure, vaultless method.
For corporations in these regions that are concerned with the integrity of their tokenization process, it is often possible to get a variance granted in the law, or to petition for an exception. For example, if the company uses tokenization in a FIPS 140-2 Level 3 validated cryptographic module, their local government will often make an exception for them.

/ds_thumbnail_kmes%20s3-min.png)
"By deploying Futurex devices, Ecentric will be the first payments provider in Africa to deploy ‘point-to-point’ encryption (P2PE), thereby establishing the strongest protection possible... P2PE will provide a competitive advantage and is a major step forward in assisting our customers..."
- Hassen Sheik, CEO
Ecentric
Futurex provides HSMs and key management servers that handle encryption, bring-your-own-key (BYOK). Futurex helps enterprise organizations deploy a modern cloud data security environment that complies with the latest standards and regulations.








