FIPS 140-2 Level 3 Compliance and What It Means for Your Security
Table of Contents
Imagine a high-security lab handling dangerous biological samples. Entry requires clearance, biometric scans, and strict protocols. Any breach triggers immediate containment.
Federal Information Processing Standards (FIPS) compliance is the same for data. It protects sensitive information by enforcing strict access controls and responding instantly to tampering attempts.
FIPS Security standards defines how encryption modules must operate to protect critical data.
FIPS compliance isn't optional for government, finance, and healthcare organizations.
What are FIPS Security standards?
FIPS, developed by the National Institute of Standards and Technology (NIST), is a publicly available security guideline for protecting digital information.

They establish clear rules for cryptographic algorithms, encryption modules, and security frameworks.
Key FIPS Security standards include:
- FIPS 140-2: Establishes security requirements for cryptographic modules securing sensitive data.
- FIPS 197: Defines the Advanced Encryption Standard (AES), a widely used encryption algorithm for securing digital communications.
- FIPS 200: Specifies minimum security controls for federal agencies to ensure baseline cybersecurity measures.
Organizations that meet these standards are committed to cybersecurity, data integrity, and operational resilience.
FIPS 140-2 Overview and Security Levels
FIPS 140-2 defines four levels of security for cryptographic modules, each building on the previous with stricter requirements:
- Level 1: Basic security requirements, including approved cryptographic algorithms and production-grade components, but without physical security enhancements.
- Level 2: Adds tamper-evident security features, such as coatings or seals, and requires role-based authentication to limit access to cryptographic functions.
- Level 3: Introduces tamper-resistant mechanisms, identity-based authentication, and stricter user verification. It also mandates physical or logical separation of critical security parameters to prevent unauthorized access.
- Level 4: Provides the highest security, requiring cryptographic modules to resist extreme physical and environmental attacks, such as temperature fluctuations or voltage manipulations.
Key Features of FIPS 140-2 Level 3 Compliance
Level 3 strikes a balance between strong physical security and operational practicality.

It's the standard for industries that handle high-value or regulated data.
Key features of FIPS 140-2 Level 3:
Physical tamper-resistanceThe hardware must be designed to prevent unauthorized physical access. This includes strong enclosures and tamper-detection/response circuitry that zeroes all plaintext critical security parameters (CSPs) if the module is compromised.
Identity-based authentication
Unlike Level 2, which requires role-based authentication, Level 3 demands identity-based authentication. This ensures that access is granted based on individual identities rather than roles.
The interfaces through which CSPs enter and leave the module must be physically or logically separated. This enhances security by isolating sensitive data paths.
Encrypted key management
Private keys can only enter or leave the module in encrypted form, ensuring that sensitive cryptographic information remains protected.
Achieving FIPS 140-2 Level 3 compliance gives organizations the confidence that their cryptographic modules can securely manage and protect data, even in challenging or remote environments.
How To Achieve FIPS 140-2 Level 3 Compliance
Achieving FIPS 140-2 Level 3 compliance demands thorough preparation, strategic implementation, and accredited third-party validation. Futurex provides solutions that simplify and accelerate this process. Here’s how compliance is achieved - and how Futurex can help:
Implement physical intrusion prevention
Level 3 compliance requires cryptographic modules to include robust physical security mechanisms that deter unauthorized access to critical security parameters (CSPs). Futurex hardware security modules (HSMs) are designed to meet this standard with tamper-evident and tamper-responsive protections. If tampering is detected, plaintext CSPs are automatically zeroized to preserve confidentiality.
Enable identity-based authentication
Unlike Level 2, which allows role-based authentication, Level 3 mandates identity-based authentication. This means each user must have a unique login credential, ensuring stricter access control to cryptographic functions.
Undergo testing and validation
All cryptographic modules must be independently tested by an accredited Cryptographic and Security Testing (CST) laboratory. Futurex's HSMs are built to meet or exceed FIPS 140-2 Level 3 standards and have undergone this rigorous testing process, giving you a head start toward certification.
Follow the CMVP validation process
The Cryptographic Module Validation Program (CMVP) oversees the certification of cryptographic modules. The process involves:
- Selecting an accredited Cryptographic Module Testing (CMT) laboratory.
- Submitting the cryptographic module and required documentation for evaluation.
- Undergoing rigorous testing by the CMT laboratory to verify compliance with FIPS 140-2 requirements.
- The CMT lab submits its evaluation report to CMVP for final review and approval.
- Upon successful review, CMVP issues a FIPS 140-2 validation certificate for the cryptographic module.
What FIPS 140-2 Level 3 Compliance Means for Your Security
Achieving FIPS 140-2 Level 3 compliance significantly enhances an organization's security posture.
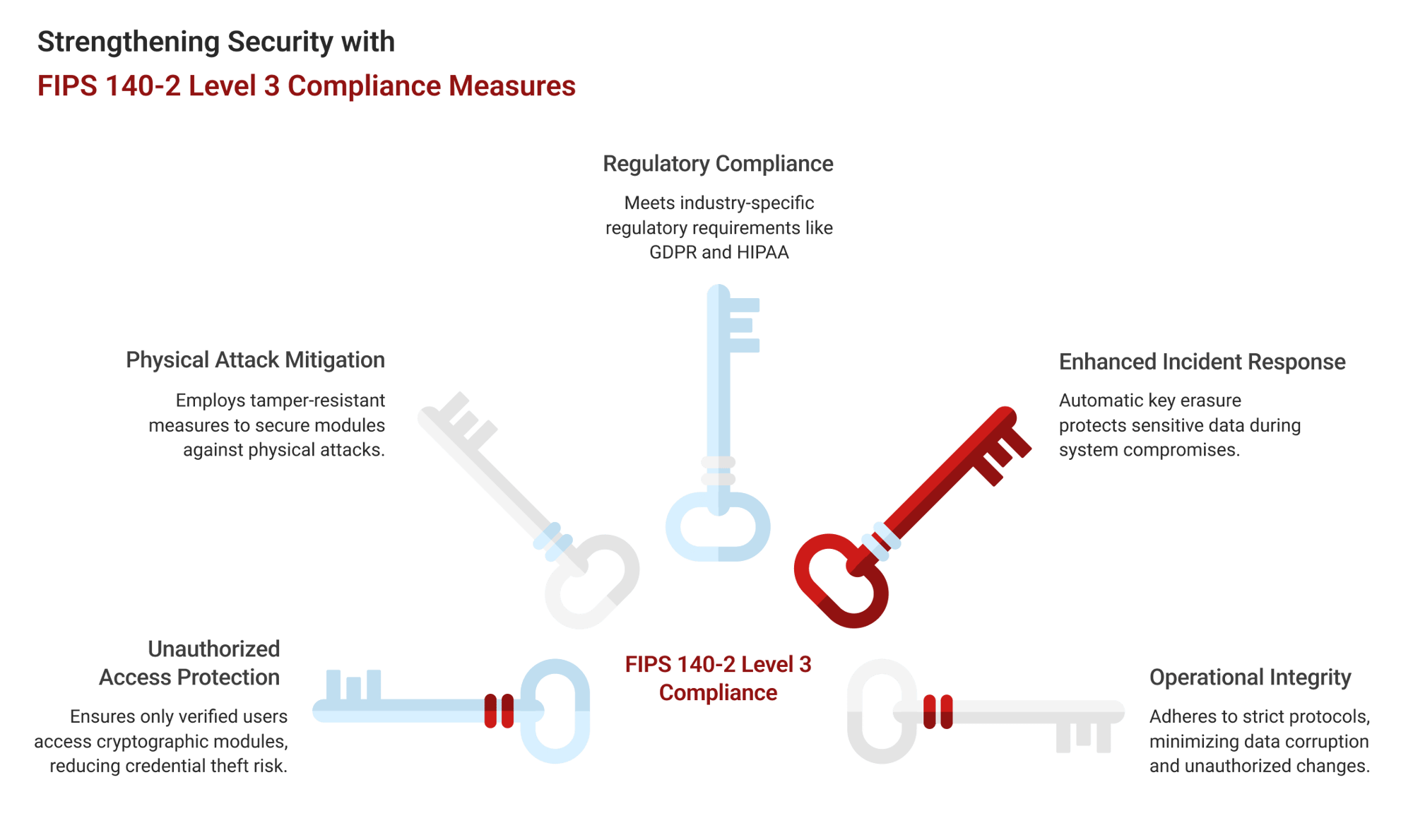
Here's what it means:
- Protection against unauthorized access
Level 3 ensures that only verified users can access cryptographic modules through identity-based authentication, reducing the risk of credential theft and unauthorized access.
- Mitigation of physical attacks
Tamper-resistant security measures ensure that cryptographic modules remain secure even under sophisticated physical attacks.
- Regulatory compliance
Many industries, including finance, healthcare, and defence, require compliance with FIPS security standards to meet regulatory obligations such as GDPR, HIPAA, and PCI DSS.
- Enhanced incident response
Automatic key erasure ensures that even if a system is compromised, sensitive cryptographic keys remain protected, reducing the impact of data breaches.
- Operational integrity
Cryptographic modules that meet Level 3 compliance operate under strict security protocols, reducing the risk of data corruption and unauthorized modifications.
Next Steps
FIPS 140-2 Level 3 compliance isn't just a checkbox - it's a foundational step in safeguarding sensitive data and defending against modern threats.
As cyber risks continue to grow, organizations need security frameworks that are resilient, compliant, and capable of adapting to future challenges.
Like a high-security lab protects what matters most, FIPS 140-2 Level 3 ensures your cryptographic environment is sealed, verified, and ready to respond. Futurex helps make that standard your reality.
